You have probably come across more popular mobile operating systems like Android, iOS, Windows, and more. But what you probably wasn’t aware of is that there are plenty of mobile OS alternatives available in the market that’s here to cater to your needs. Though the Android and iOS are dominating in the mobile phone industry, KaiOS, Ubuntu Touch, Symbian, and Blackberry OS are worth taking a deeper dive into it. Especially given that these are quite popular ones in other countries out of the United States.
That said, if you ever need to expand your knowledge on Android, iOS, Windows, and even more, we got you covered. Expect to find the latest updates on the Apple iOS 13, Android 10 mobile operating systems and we help you uncover hidden tricks to get the most out of the mobile OS. However, if you simply didn’t like the existing mobile upgrades and wished to downgrade your mobile firmware, we’ll show you exactly how to downgrade your iOS easily.
 What is A Mobile Operating System (OS)?
What is A Mobile Operating System (OS)?
The first question you should be asking is what is a Mobile Operating System and how does it work? When it comes to the mobile OS, we usually think of the system that runs our phones. However, the truth is these operating systems like iOS, Android, and does more than just on smartphones. In fact, these mobile operating systems are also applicable to tablets, smartwatches, phablets, and more.
Technically, your phones or devices can’t operate without the proper installation of a mobile OS. What it does it’s simple, it mainly serves as your phone’s mainframe to support your mobile activities. Besides, your mobile OS is also responsible for connecting the hardware to the application. In layman terms, try to think of it as a middleman that bridges the gap of your phone’s hardware and software. Hence, that is the reason why smartphones are getting more versatile as these mobile operating systems are constantly improving.
In most cases, when you purchase a mobile phone with the preferred choice of an operating system, you’ll find native apps that come along with the device. For example, you’ll find an Apple TV app pre-installed on your iPhone while Google’s apps pre-installed in all Android devices.
The Evolution of Mobile Operating System
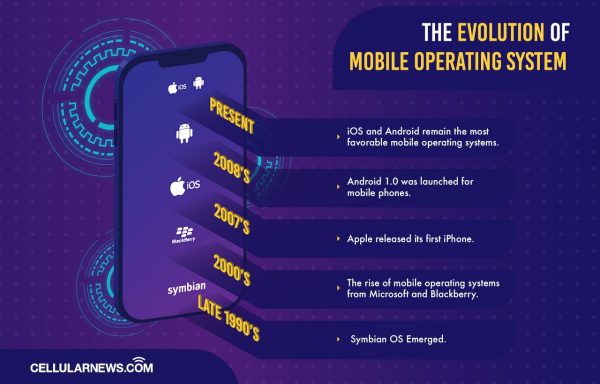
We cannot look at the current state of Mobile Operating Systems without looking at the past. Android, iOS, and every modern OS drew inspiration from their past counterparts. Back then, mobile phones had simpler functions and that is to help us get connected. Besides the basic functions of calling, answering phone calls, and receiving messages, at most you’ll just play ‘The Snake’ game on the phone.
Before mobile phones took a turn to the Millenium, it mostly ran on embedded systems. An embedded system usually features a processor, input, output, and memory which is commonly seen used on portable music players and vehicles. Soon after, mobile operating systems evolved in the form of Personal Digital Assistants. What it does are far more sophisticated than the basic is by allowing mobile devices to organize emails and gain internet access. At that time, the most popular OS for PDAs was the PenPoint OS.
Then a few years later, Symbian OS emerged during the mobile blooming era of the late 1990s and early 2000s. Symbian was a cooperative effort from Nokia, Motorola, Ericsson, and PSION. That said, these three brands gains it’s popularity mainly during the rise of Symbian.
The 2000s also saw the rise of mobile operating systems from Microsoft and Blackberry. But, in 2007 Apple released its first iPhone, and with it is Apple’s iOS changed the whole landscape. The iPhone combined cell phone functionality with iPod and internet capabilities. Soon enough in 2008, Android 1.0 was launched for mobile phones and subsequently for tablets and other mobile devices.
Until now, iOS and Android remain the most favorable mobile operating systems. And though these two OS seems to be a constant rivalry, a healthy competition doesn’t hurt.
 What Are The Functions of A Mobile OS?
What Are The Functions of A Mobile OS?
If you’re familiar with a computer, a mobile operating system needs to boot-up and to operate. Without an OS, your phone wouldn’t function properly not to mention the other applications. Though some mobile phones come with a specific OS, some rather rely on the universal OS like Android. That said, if the iPhone runs on iOS, it’s mobile apps will not function on Android. For an application to function as it supposed to be, it has to compatible with the designated operating system.
Generally, a mobile operating system is responsible for determining the functions and features available on your device. While the main difference of an OS from one another is much more prominent on their thumb wheel, theme settings, keyboards, WAP, synchronization with applications, navigations, and more. Another worthy note is the mobile OS will also determine which third-party applications is the best fit on your mobile phone.
So, if you’re keen on getting a mobile phone with the best navigation or flexibility to customize, a mobile OS should be the main determining factor.
 What Is An Open-Source Operating System?
What Is An Open-Source Operating System?
Have you ever wondered why so many manufacturers use Android as their main operating system? Well, that is because Android is an open-source operating system. But before we discuss further, we need to know what an open-source operating system is.
There are two types of operating systems, closed and open. Closed or proprietary operating systems are exclusive to the developers of the OS. This means that they are the only ones that can open and modify the OS’s source code. Open-source operating systems, on the other hand, can be modified by anyone. The source code within the OS can be studied and edited by a third-party.
Another difference is when you are using a proprietary OS, you should agree to the terms set by the original developers. But, for an open-source OS, you can modify the code itself to suit your purpose.
Hence, if a user prefers customizable mobile phones often opt for Android, PureOS, Tizen OS, Sailfish OS, and more. That also means, if you’re a developer who knows how to create apps based on the operating system, you’re free to do so without facing any legal troubles. The upshot? Android is available for free and is open to anyone who wants to study or modify its coding.
 What Are The Best Mobile Operating Systems Now?
What Are The Best Mobile Operating Systems Now?
The best mobile operating systems is highly defined by a user. Some argue iOS is best while some support Android. We think the best mobile OS is based on what works best for a person and in certain conditions that best fit the objectives and a goal to ease the hassle. If you insist, Android and iOS is among the best that you can’t omit. In terms of performance, versatility, design, and approach, these 2 mobile operating systems are on par with each other. If you needed reasons to know why they are among the best, here’s the analysis.
Android OS
Android is an open-source operating system built for mobile devices. This operating system was launched in 2008 it made its first appearance in the HTC Dream. Initially, Android uses Linux kernels and has seen many upgrades throughout the next decade.
However, being an open-source operating system, Android is popular among developers, manufacturers, and consumers. Mainly because it allows developers to create a user interface for their devices based on Android. Though Android is most popular on mobile phones, this mobile OS works on tablets and smartwatches too.
The common partnership for Android is seen on Samsung, LG, Huawei, Xiaomi, Vivo, and more. If you’re keen to check out some of the popular Android mobile phones, we listed a few down below.
Who Developed Android?
Android OS was initially developed as an operating system for Digital Cameras. But, with the mobile phone boom of the 2000s, the developers then changed their plans. They then decided that Android will cater to smartphones. Android was acquired by Google in 2005 and spearheaded a consortium of developers to further develop the OS.
This group of developers is known as the Open Handset Alliance or OHA. The majority of the developers in the OHA are from Google. While the rest are from other manufacturers and app developers.
What Are the features of Android OS?
The main feature of Android is that it’s an open-source program. This allows any interested party to change it to their liking. Another feature of the Android OS is that most of its devices have Near Field Communication capabilities. This allows devices to interact with each other while in close proximity to each other.
Android devices also allow many keyboards, unlike other operating systems. The operating system allows the installation of different keyboard styles and apps. This is great for users who prefer different kinds of keyboards. Customizable themes with unique icons, accessibility, privacy settings, and so on. If you want to upgrade your hardware, Android devices allow its users to change the stock batteries.
What is the Latest Android Version?

The Android operating system has seen a lot of upgrades since its inception. There were two separate versions of OS that run on different devices. The Android Gingerbread and Honeycomb ran on smartphones and tablets respectively. But, this all changed with the release of the Ice Cream Sandwich update.
The Ice Cream Sandwich update combined the two different versions of Android into one another. This is now the norm for both phones and tablets, every update since the Ice Cream Sandwich applied to both devices.
The latest major Android update arrived in September 2019. With past versions having dessert nicknames, the new version had a very simple name. The latest version of the mobile operating system is known as Android 10. If you want to know more about Android 10, we have a guide to help you out.
What are the Past Android Versions?
Android has undergone many upgrades and different versions. That means you’ll find many versions throughout the years. Here are some of the Android versions you’re looking into.
- Cupcake
- Donut
- Eclair
- Gingerbread
- Honeycomb
- Ice Cream Sandwich
- Jelly Bean
- KitKat
- Lollipop
- Marshmallow
- Nougat
- Oreo
- Pie
- 10
How to Install Android OS?
Most Android devices come with a built-in operating system. This version is relative to the model of your device. Older devices will come with obsolete versions of Android and the opposite goes for newer ones. But like all devices, the system is not perfect and you might need to reinstall the OS after a reset.
There are two ways that you can install or reinstall Android OS. These two methods will require you to back up your files and stock ROM. Then, you will have to “factory reset” your device which will then wipe everything on your phone. To do this, press the volume down and off buttons at the same time. Next, you’ll see a custom recovery interface. This is the part where you can reset your device to its factory settings.
You then have to clear everything on your phone before you can start reinstalling the OS or a custom version of it.
Installing Android Without a PC
For those that don’t have a PC, you can save your Android ROM on your SD card. Then, choose the setup option you want and pick the ROM on your SD card. Finally, all you need to do is wait until the installation process is completed.
Installing Android Using a PC
For those that have a PC, you’ll need to connect your device to your computer via USB. You’ll first need to turn on developer mode on your Android device. You can find this option when you access the “About Phone” option on your Settings. When in developer mode, you can then turn on the “USB debugging” under the debug menu.
You will then need to download an Android SDK tool on your computer. Next, you’ll need to open the SDK files on your computer. Lastly, you’ll need to restart the device to enter recovery mode which will allow you to access the ADB reboot recovery.
All you need to do is the factory reset your phone and the OS will now start installing.
How to Update Android OS?
So, you want to have access to the latest Android version and all its features? However, your current version is obsolete and not compatible with newer features. All you have to do is update your phone through your settings. Provided that you are not using any custom or a rooted version of the Android OS.
Just go to your settings, then access the “Software Update” option. This will allow you to download updates manually, automatically, or schedule updates.
Take note that some devices may not be compatible with the latest update.
How to downgrade An Android Firmware?
As an Android user, you can also downgrade your OS to a previous version. To do this, you’ll need to download a copy of a previous version’s ROM on your PC. Then, you’ll also have to get a Flash tool for your PC. Once you’ve got both sets of files, extract them, and use the Flash tool to access the firmware file.
Then press the off and volume down buttons on your phone. Next, press the volume up button when a prompt is shown, your device will now be on Download Mode. You will then need to connect your device to your computer via USB. You can now flash your phone to install the older version of Android. Lastly, your phone will now reboot and once it’s up, it’ll be on an older version of Android.
There are other ways of downgrading your OS and you might want to try that if flashing won’t work on your phone. If you’re interested, we have a how to downgrade Android firmware guide that can help you out.
How to Root Android Phone?
Rooting is the method of attaining special permissions on your Android devices. This will allow the user to change the settings of their phones that are out of limits to most consumers. These limits were probably set by the developers and manufacturers of a specific device. This is possible with both Android and iOS devices. However, the act of rooting iOS devices is called jailbreaking and we’ll get to that later.
To root your Android device, you’ll need to access the developer options. Then, you’ll need to download tools such as SDK Platform-tools and device drivers. Next, you need to access your device’s bootloader. Depending on your phone’s brand, you might want to download a third-party program for this step. Once you’ve accessed your bootloader, you can now use a third party program to root your device.
If you want a more in-depth guide on how to root your Android phone, we have an article that can help you out. We also have a guide talking about 15 Best Root Apps you must download.
The Pros & Cons of Rooting Your Mobile Phone
There are several pros and cons that you once decide to root your phone. It is better to research ahead and see if the pros outweigh the cons. The positives are a definite plus but rooting can result in your phone receiving permanent damage.
| Pros | Cons |
|---|---|
|
✅Remove limitations set by manufacturers and developers.
|
❌Safety risks as a result of Security Apps being disabled.
|
|
✅Ability to customize settings that are normally out of reach.
|
❌Possibly bricking your device and inducing permanent damage.
|
|
✅Installing programs and modifications to your device.
|
❌Voiding your device’s warranty.
|
How to troubleshoot android System errors?
If you ever feel like your Android device is slowing down, it can be a result of low memory space or too many apps are open. If you have unwanted files, you can delete them to make space for your storage. You can also close apps that you are not using to further improve your device’s performance.
If you want a more all in one fix, you can use your Device Maintenance feature. This will allow your device to clear unwanted programs and tasks. This will help you to optimize your device’s performance.
To access this, go to your settings and press on Device Maintenance. Then, you’ll see your device’s current efficiency. Press Fix Now and your phone will then free up storage and memory, as well as look for malware. This method will also help you save your battery as it turns off unused apps.
Accessing your Device Maintenance feature often will lead to your Android device to work efficiently.
Apple iOS
Apple’s iOS is an operating system created and developed by Apple. Previously known as iPhone OS, it was specifically designed to run on Apple’s iPhone. As the years went on, Apple has incorporated the OS to other products such as their iPad. While the first iOS was launched in 2007 along with their first iPhone.
The main intention of this launch was to mix the capabilities of a Mac computer with the features and portability of the iPod. The iPhone was designed to be a powerful and responsive phone that can also play media with the iPod’s clarity.
But with the launch of iOS 13, Apple restricted the update to iPhones with 2GB RAM available. This meant that older models will never have access to the upgrade. Another thing to take note of is that iOS 13 is only for iPhones and iPod touch models. The iPad now has a dedicated OS which is called the iPadOS.
IOS is a Unix-like program much like its predecessors, Darwin, and macOS. Also, it uses a proprietary source program as its base. Unlike Android, iOS can only be edited and changed by the developers at Apple. This is evident with the majority of apps that were developed by Apple for their mobile devices. However, this operating system also has third-party properties.
The iOS was also modified by Apple to power its Apple Watch. Renamed as WatchOS, this OS is compatible with your iOS devices. This makes the syncing between Apple gadgets easier. Learn more about the latest Apple’s iOS 13 here. If you’re unsure if you want to upgrade from iOS 12 to iOS 13, read more here.
Here is a list of Apple products that run on iOS that you might want to check out.
Who Developed iOS?
iOS is a proprietary-sourced mobile operating system that was developed by Apple. The idea behind its development is for Apple to empower its line of mobile phones with features from both the Mac and the iPod. Apple wanted the features of their MacOS with the media playing capabilities of the iPod. This turned out to be an all-in-one package that allows their users to be productive, play games, and listen to songs.
Over the years, Apple has integrated iOS to many devices. This list includes the iPod and the iPad. But, Apple developed the iPadOS to cater to their brand of tablets. Apple also has the Watch OS which is for its line of smartwatches. These Apple Watches can be synced to your device. You can then receive smart notifications to alert you even if you’re away from your phone.
Main Features from the apple’s iOS
Apple iOS has numerous features that were integrated throughout the years. And their features have undergone tremendous changes for good. Here are some of the main features you should be looking out.
Touch-centric Capabilities
Most of the phones during the 1st iPhone’s launch relied on buttons. These buttons were used for typing, browsing the interface and playing games. The 1st iPhone broke out from the norm and Apple implemented touch-centric capabilities for its mobile OS.
This development allowed the iPhone to have a bigger screen than most of its competitors. Also, people can now scroll the interface with a swipe and type using a virtual keyboard.
The Introduction of Folders
During the launch of iOS 4, the introduction of folders allowed users to place more apps on their home screen. This update also introduced multitasking options. This allowed users to switch from app to app without restarting the program.
Upgraded Security Features
iOS is rated to be the most secure mobile operating software ever built. As one of the first to introduce Face ID recognition, iOS is actively enhancing its mobile security in its latest iOS 13.
Siri Voice Command
the introduction of Siri was a welcome addition to iOS devices. This allowed users to use voice commands and get what hassle-free.
The difference between iOS and iPad OS
With the launch of the iOS 13, the operating system is now available for iPhone and iPod only. However, the iPad will now have a separate OS that aims to optimize the device’s features. This operating system is called the iPad OS.
This iPad-only version of the iOS 13 gives its owners the ability to pin widgets to their home screens. The iPad OS also has a split-view feature that allows its users to use two apps at the same time. This allows people to multitask even more.
Speaking of multitasking, another great feature of the iPad OS is that you can scroll through open apps. You can now swipe left and right if you ever need access to a certain app then switch it back in a matter of seconds.
The iPad OS also looks to improve your device’s performance as well as opening apps faster compared to iOS 12 updates.
How to Install Apple iOS?
All iOS devices come with a pre-installed version of the operating system. Older models will usually come with an older version of iOS. Newer models will come with a more updated version of the OS and will be suited to accommodate most of the upcoming patches in the future.
When you purchase an iPhone 11 today, it’ll come with iOS 13 already installed into the system.
Since iOS was meant to run on Apple devices, installing it on other phones is not possible. This is due to the design of the hardware and firmware itself. However, you can upgrade the version you have right now to the latest update. All you need is a compatible iPhone or iPad and to backup your files.
How to Upgrade IOS?
If your device is compatible with the update, the next thing you do is backup your iPhone, iPod, or iPad. You can backup your device via iCloud or through the computer.
If you want to update your device without connecting to a computer, you can just go to your settings and click on General. After that, you’ll want to click on Software Update to start the downloading process. Once done, you can schedule when you want the installation process to happen. Make sure that your phone is connected to a charger if you’re planning to do it immediately or overnight.
If your device currently has iOS 12, you can automatically update your device.
If you want to use a Mac or PC, you’ll either need Finder or iTunes. For newer versions of Mac, all you need to find is the Finder program. For older versions and PCs, you’ll need to have iTunes installed. Then, once you connect your phone you can now start the update.
How to Downgrade IOS?

If you are more comfortable with a previous version of iOS, then you might want to downgrade the version you have right now. Before you think of downgrading the current iOS version you have, do not forget to backup your files. If you’re looking for a past version of iOS, you can find them online. Make sure to select a file that is compatible with your device.
Make sure your device is connected to iTunes and then placed in recovery mode. Boot your iTunes and you’ll now have to restore your device. You should open the iOSIPSW file you’ve downloaded then press recover on your iTunes.
There are other methods available offline but if you’re interested we have a guide that can help you out. If you’re interested in learning how to downgrade iOS using SHSH2 Blobs, here is a guide that you can check out. Here is also a detailed guide on how to downgrade iOS using other methods.
How to Jailbreak IOS?
Jailbreaking is the method of bypassing the restrictions set by Apple developers. Once you jailbreak your device, you will now have special permissions that other users don’t have. You will have the ability to install apps that cannot be purchased or downloaded through the app store.
If you’re interested in jailbreaking your phone, here’s how to jailbreak the iOS guide to help you out.
How to troubleshoot iOS System errors?
If your iOS device is experiencing problems and dips in performance, then that’s a reason to be alarmed. Newer Apple devices have impressive specs compared to its competitors. The most frequent thing to do in this situation is to close all open apps and free up space from your storage. This means deleting unwanted files and apps.
You can also restart your phone and clear out all active applications and tasks. Another good way of optimizing your device is by installing the latest update possible.
If all else fails, you might need to visit an accredited Apple service center and have them take a look at your device.
 Android vs iOS: Which Is A Better Mobile Operating System?
Android vs iOS: Which Is A Better Mobile Operating System?

Android and Apple’s iOS has been the leading pack in the mobile operating systems industry. The Android VS iOS debate has been going on for years. People are asking which OS is better overall ever since these two emerged as the leaders of the new generation.
Mobile OS Market Share Statistics
In terms of statistics, Android has the biggest market share percentage for all mobile operating systems. According to gs.statcounter.com, Android has the biggest market share when it comes to mobile operating systems. From February 2019 to February 2020, Android 73.3% market share with iOS only coming in at 25.89%.
One main factor that could have affected this is that Android is used by multiple brands. Being an Open-Source program has allowed developers to use it as a base for their UI. With 6 major brands using the OS, it is no surprise that Android leads the way in terms of Market Share.
Another major factor could be the price of Android devices compared to iOS ones. Apple devices tend to be costly. While multiple Android devices can match them in terms of price, there are also mid-end and low-end Android options. This allows the OS to have a bigger target market.
Comparison of Mobile Operating System
If we compare both operating systems, there are a lot of pros and cons of choosing one of the two. Some features of iOS are better than those from Android and vice versa. Sometimes, choosing a mobile operating system will come down to your lifestyle.
If you want a more customizable OS, then Android is the one for you. However, if you prefer more security and more lifestyle options, then iOS is for you. Not convinced? Here’s the in-depth comparison of Android VS iOS from its Apps store, accessibility, voice assistant, cloud service, and more…
 Other Mobile Operating Systems
Other Mobile Operating Systems
Believe it or not, there are lots of other options when it comes to mobile operating systems than you ever expected. If you’re interested to try something out of the ordinary, here is a list of operating systems that should pick up your curiosity.
Harmony OS
Harmony OS is a mobile OS developed by Huawei after the US government placed a trade ban on Huawei products. Because of this, Google stopped providing support and services for Huawei products that run on Android. As a result, Huawei sped up the development of its OS, Harmony.
Harmony is a microkernel-based system that will be available for free. This operating system will run on phones, smart TVs and smartwatches. The goal of this OS is to not replace Android but rather evolve from the popular OS. Harmony aims to provide a quality user experience. This is possible through the inter-connectivity of their products.
It also aims to provide users with increased performance efficiency compared to Android. Huawei is aiming to decrease task delays and will prioritize higher-level tasks.
Currently, the Harmony OS is only available on Huawei Smart TVs but will soon be built-in into their smartwatches and smartphones. If you are interested to know more about the Harmony OS, we have an in-depth article that you might want to read.
Blackberry OS
Blackberry OS is a mobile operating system that is developed by Blackberry Limited and it was once the top in the smartphone industry. This is due to their OS and phones’ multitasking features. Most blackberry phones feature trackpads and trackballs to navigate the different apps on the phone’s user interface.
Just like Apple iOS, Blackberry OS is also a proprietary operating system. This means that the development and modification of the OS will only be handled by Blackberry’s developers. Third-party app developers can create apps for Blackberry products by undergoing Blackberry API classes.
The latest version of the OS is named Blackberry 10. In later updates of Blackberry 10, Android apps can now run due to a similar runtime. However, Blackberry Limited will only look to support the OS until 2020. Also, major services have stopped receiving support as 2019 ended.
If you’re interested to know about the Blackberry OS and the products that use it, you may check out our article that focuses on the topic.
Windows OS
Windows Mobile OS was a mobile operating system developed by Microsoft to power Windows mobile devices. The last major update for the operating system was the Windows 10 mobile. This update aimed to match up to its PC counterpart. Windows 10 mobile also provided its users with better syncing with the PC version.
Windows has now opted to use the Android mobile operating system for their mobile phone. This will all start with the release of their newest phone, the Surface Duo. Windows tablets that have dual-screen capabilities will run on the new Windows 10X OS.
Symbian OS
The Symbian OS was the most popular Operating system during its peak. Back then, Nokia, Sony Ericsson, and Motorola were the biggest names in telecommunication devices. These 3 companies partnered with Psion Software to form Symbian ltd.
One of the reasons why Symbian was very successful is due to its features. One of its main features was the Opera browser that allowed mobile users to surf the internet using their phones. Another cool feature of Symbian is its very helpful interface and app development.
Products from Nokia, Sony Ericsson, and Motorola all used to run using the Symbian OS. Want to know more about Symbian? Well, we have an article that can give you a more in-depth look into Symbian OS.
KaiOS

KaiOS is emerging as the third most popular mobile operating system behind Android and iOS. KaiOS is a Linux-based operating system and was launched in 2017. This operating system aims to cater to phones with physical keypads. It may seem obsolete but don’t judge a book by its cover. KaiOS-powered devices have the functionalities of smartphones. They can connect to the internet and access social media apps.
Another great feature of KaiOS is that it does not require a lot of memory space. This means your phone can run more efficiently. KaiOS phones also use up less battery life and can last longer than smartphones.
Currently, KaiOS is popular with people from Asia, India, and Africa. In terms of products, there are Nokia and Alcatel phones that run using KaiOS.
Lineage OS
Lineage OS is an open-source mobile operating system. It is based on the Android OS and is available for free. Lineage works on phones, tablets, and tabletop computers and is an open-source operating system. Launched in December 2016, Lineage OS’ has made its source code available through many platforms.
The main feature of Lineage OS is the absence of “bloatware”. This type of software is usually pre-installed in most phones and is often deemed unnecessary. Lineage OS-run devices have the usual features of a smartphone such as messaging, a mobile browser, and camera functions to name a few.
Lineage is compatible with a lot of Android phones and can be installed for free.
LuneOS
LuneOS is a mobile operating system for smartphones and tablets with touchscreen capabilities. This OS is Linux kernel-based and is continually being developed by WebOS-Ports
The latest major update of the LuneOS is called Doppio.
WebOS
WebOS has been through a lot of changes throughout the years. This Linux kernel-based operating system was first developed by Palm Inc. Hewlett-Packard acquired webOS and made it into an open-source operating system. LG would, later on, acquire the OS and the current owners of its patents are Qualcomm.
Currently, webOS is primarily used on Smart TVs and has also seen use on phones.
PostmarketOS
PostmarketOS is an open-source mobile operating system that was launched in 2017. Postmarket OS is an Alpine Linux-based OS that runs on smartphones. TheThis OS aims to create a decade long lifespan for smartphones. One of its main features is it allows different interfaces from X and Wayland to run on your phone.
The developers of the operating system avoided copying Android’s build system. Instead of one big file, POstmarketOS has divided their whole OS into bits and pieces.
The packages of data can be installed on other devices that share the same CPU architecture. PostmarketOS is available for free and can work on a huge number of devices. This list includes the Nexus 5, Nokia and Asus phones.
Ubuntu Touch
Ubuntu Touch is an operating system from Ubuntu that caters to mobile devices. Ubuntu’s original developer was Canonical Ltd. but when the company stopped supporting the OS, the UBPorts community continued the development of the OS. Ubuntu Touch is an open-source operating system whose main goal is to provide a different approach when it comes to user experience.
Instead of apps, Ubuntu Touch uses scopes that aim to simplify content delivery. What’s great about Ubuntu Touch is that you can modify the OS to better suit your demands. Ubuntu Touch can run on many products, such as phones and tablets.
If you want to learn more about Ubuntu Touch, you can read our beginner’s guide to the OS.
Pure OS
PureOS is an open-source operating system that can work on computers and smartphones. This operating system runs on a Linux distribution and utilizes the GNOME desktop environment. This operating system is designed to only include open-source and free software.
The main feature of PureOS is its emphasis on user security and privacy. Its browser, Purebrowser, is similar to Firefox but has an increased focus on privacy. If you’re interested, you can install the OS on both your phone and on your PC.
But, the OS also comes built-in when you purchasePurism’s Librem 5 phone.
/e/ aka Eelo
/e/ is a mobile operating system that borrows from LineageOS. This operating system used to go by the name Eelo and aims to make technology that respects the privacy of its users. However, /e/ does not market themselves solely as an operating system. /e/ wants to market itself as a privacy software that develops operating systems, codes, and apps.
This mobile operating system is free and is compatible with 85 smartphone models.
Sailfish OS
Developed by Finnish company Jolla, Sailfish OS is a mobile operating system that values data privacy. This mobile operating system follows a regional licensing model. Sailfish is a flexible OS that can be installed on other devices.
A testament to Sailfish OS’ flexibility is its compatibility with Android, whether via hardware or software levels. Android designed apps can run on this operating system even if it’s independent of the more popular OS.
Sailfish OS can be installed on numerous phones with the Sony Xperia models being the most prominent. If you’re interested to know more, we have an article that takes a deeper look into Sailfish OS.
Plasma Mobile OS
Plasma Mobile is the portable version of the Plasma Operating System. This operating system is an open-source OS that takes pride in its flexibility. You can customize the interface to suit your needs and preferences. It is compatible with KWin and Wayland interfaces.
Plasma Mobile also uses powerful software tools from known names to power-up its performance. This includes Telepathy, Pulseaudio, Ofono, KDE Frameworks, and Kirigami.
The Nexus 5X is compatible with Plasma Mobile.
MeeGo
MeeGo was a mobile operating system that was hosted by the Linux Foundation and was made use of the Moblin and Maemo operating systems’ source code. This OS was designed to be compatible with numerous devices such as smartphones, computers, tablets, and smart TVs. MeeGo was the result of Intel and Nokia wanting to combine the properties of their respective OS, the Moblin, and the Maemo.
MeeGo was replaced by another OS, Tizen. But before it folded, Nokia released the N9 which was powered by MeeGo.
Tizen OS
Tizen OS is a mobile operating system that is developed by Samsung and backed by the Linux Foundation. Originally, Tizen was supposed to replace MeeGo but Samsung combined its Bada OS into the project. Albeit being an open-source OS, Samsung has proprietary components built into Tizen.
Tizen is currently being used by Samsung on three products manufactured by the brand. Tizen can be found on Samsung Z series phones, smartwatches, and cameras.
Smartwatch OS

Speaking of operating systems, we can’t forget about smartwatches. Smartwatches are constantly being paired up with smartphones to increase the accessibility of our mobile devices. However, some manufacturers use a different OS for their Smartwatches. An example would be Samsung as most of their phones run on Android, their smartwatches, however, use the Tizen OS.
Here are the operating systems used by some of the biggest manufacturers of smartwatches.
If you’re looking for a comparative guide, here’s our article pitting Wear OS VS Tizen.

Smartwatches OS
- Google – Wear OS
- Samsung – Tizen OS
- Apple – Watch OS
- Garmin – Garmin OS
- Fitbit – Fitbit OS
![]()
Active Mobile OS
- Android, iOS
- Harmony, Sailfish OS
- KaiOS, Ubuntu Touch
- LuneOS, Lineage OS
- TizenOS, /e/
- PostmarketOS
- PlasmaMobileOS

Inactive Mobile OS
- Symbian
- The Blackberry OS
- Windows
- WebOS (only available on TV)
- MeeGo OS
 Benefits of The Mobile OS Based on Its Functions
Benefits of The Mobile OS Based on Its Functions
Let’s be real here. There’s nothing perfect and the same theory applies to the mobile operating systems. There are always advantages and disadvantages when it comes to certain aspects. While some operating systems are better suited to host apps and play games. The other might be better for something else.
We will now take a deeper look at what OS you should consider using based on your needs and interests.
Best Gaming Mobile OS
In terms of gaming, Apple’s iOS and Google’s Android lead the heap of operating systems. Mobile games have seen a drastic evolution with their graphics and functionality. But, these improvements will need more from your hardware and software.
Apple’s iOS might be a stalwart when it comes to gaming but Android is currently the OS of choice for the top gaming phones. The list of gaming smartphones that use Android includes the ROG Phone 2 and the Razer Phone 2. These phones are targeted to cater to mobile gamers.
But iOS devices tend to have better specs that can only be matched by the top of the line Android phones.
Don’t be fooled, these criteria is close and may just go according to your preference.
If you want to experience top-flight mobile gaming, you might want to check these phones out.
You can also check out our list of the best gaming phones to look out for in the market.
Best Mobile OS for photography
Photography has been one of the strong suits of the Apple iOS. Aside from numerous enhancements to their camera features, there are also more photography apps on the Apple App Store. Also, the iOS 13 and iPad OS updates made it even easier to find photos due to its photo curating feature.
If you’re a mobile photography hobbyist, Apple’s iOS might be the one for you.
best mobile oS for productivity
If you’re the type of person who uses his phone as part of his daily work routine, then this section is for you. If you think about it, most smartphones nowadays function like smaller computers.
When it comes to productivity, having a smoother transition from app to app is essential. You’ll find the need to have easier access to your email, organizers, and planners. Aside from having an easier transition between apps, Android’s Gmail has a bigger storage space for emails. Also, Android phones have better Maps features and Cloud Services.
best mobile oS for Entertainment
When it comes to entertainment, it all boils down to playing music and streaming videos. Newer smartphones have better screen displays than their predecessors. Images become crisper and users can now see the finer details. Both Android and iOS devices have provided their users with the ability to watch movies and videos with clarity.
In terms of streaming music, both have their music streaming service and can accommodate third-party ones.
the overall best mobile operating systems
The standards Android and iOS have set are quite high and picking between the two is hard. Add the fact that other mobile operating systems specialize in other factors such as security and adaptability. Picking the best mobile OS might end in a toss-up or to what your lifestyle requires.
As of now, Android and iOS is dominating the market. While iOS is only compatible with Apple’s product, Android is more versatile and can be seen operating on Samsung mobiles, Vivo, LG, and more.
Apple’s iOS is a pivot player in the mobile operating systems industry. Apple prioritizes their user’s security more securely through their constant updates and implementation of security features. Hence, the introduction of face recognition ID, touch-ID, and so on. As for Android, it utilizes similar features it encrypts data too. But not all is securely encrypted. That means Android users are still prone to security breaches. Mostly because Google A.I. collects the data to serve better ads target.
Yes, but it’s very unlikely. Again, Apple focuses very much on security, meaning the virus is a big no-no. Most iPhone users don’t have to worry about getting a virus on their mobile because the architecture of the iOS operating system restricts these malicious programs run on the iPhone at all. Besides, Apple evaluates all apps carefully before it’s released on the Apps store.






















